Show run vs “more:”

To read a file’s raw contents that are stored on a Cisco router, switch or firewall’s local storage system, issue the “more” command and the file’s contents will be displayed on the CLI. This may be particularly useful for you if you’re setting up a VPN or need to rebuild a AAA group (TACACS or RADIUS) or viewing context configs on an ASA. Both the “show run” and “more” command outputs can be modified by using the pipe command ( | ). See the examples below:
So let’s hop over to to the lab and check this out. We have an ASAv running with just a single tunnel-group configured for this example called “KEYEXAMPLE”. When we run the regular “show run” command on the tunnel-group, we get the following output.
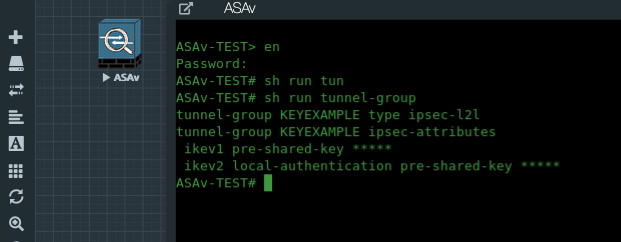
Although this is useful to see that we have keys defined, we cannot see them. Unfortunately, we cannot see the keys stored in the running config. This is done for security reasons that I won’t get into at this time, but when you’re trying to troubleshoot a vpn key mismatch, you may want to grab the keys from the running config and compare them in notepad++. So, how do we do that?
So, let’s try using the “more:” command in this example. On the ASAs, we need to specify “more system:running-config” as the command to see the raw output of the actual running-config.
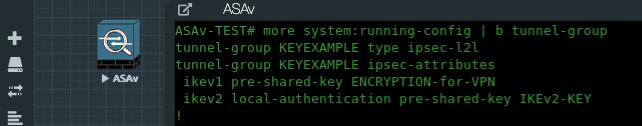
Networking Enthusiasts rejoice!! This makes troubleshooting a lot easier, especially if you are working on a production issue. After issuing the “more system:running-config” command, the ASA will display it’s actual pre-shared-keys as well as any other starred out data with regards to TACACS or RADIUS server keys. Play around with this command on the ASAs, routers and switches.
(Note: I put both IKEv1 and IKEv2 keys in this example just to demonstrate it will work with both. In production, please use IKEv2).
Wrap up: So, I wanted to publish this article to hopefully shed some light on how to quickly view the starred out data on ASAs. You can also use this to view the contents of text files stored on flash of routers, switches and firewalls. Commands used here:
Useful commands from this example:
show runsh run tunnel-groupmore system:running-config